Accelerating blue team response times through asset tagging
Blue teaming is tough work. The attackers have all the time in the world, and only need to find one way in. Whereas the blue team needs to protect all the attack surface, all the time. And when an incident does occur, they’re against the clock to analyse, identify cause, and then balance any direct impact, against the indirect impact of taking services offline etc.
It’s pretty obvious that anything that hinders the analysis and response will make the task harder, slower, and will potentially increase the impact too.
From talking to various blue teams, one thing that consistently makes the response process harder, is identifying asset owners and getting decisions made quickly. Which is made all the more difficult with the move to the hybrid-cloud, remote-working, and automation. Asset lists are often duplicated, incorrect, or hopelessly out of date, and the dynamic nature of the cloud can mean that an address will have already been recycled (and so no-longer exists within your cloud consoles).
scarlet can help to make these issues a thing of the past, through synchronising your assets in real-time with your SIEM, and exposing the cloud-native tagging at the same time. And what’s even better, is that it literally takes minutes to enable, and requires no effort from your blue team to derive the benefit. What’s not to like about that?
Eating the dog food
As an example of how easy this is, let’s go through the process of tagging the assets, connecting scarlet to Microsoft Azure and Sentinel, and seeing what an event looks like.
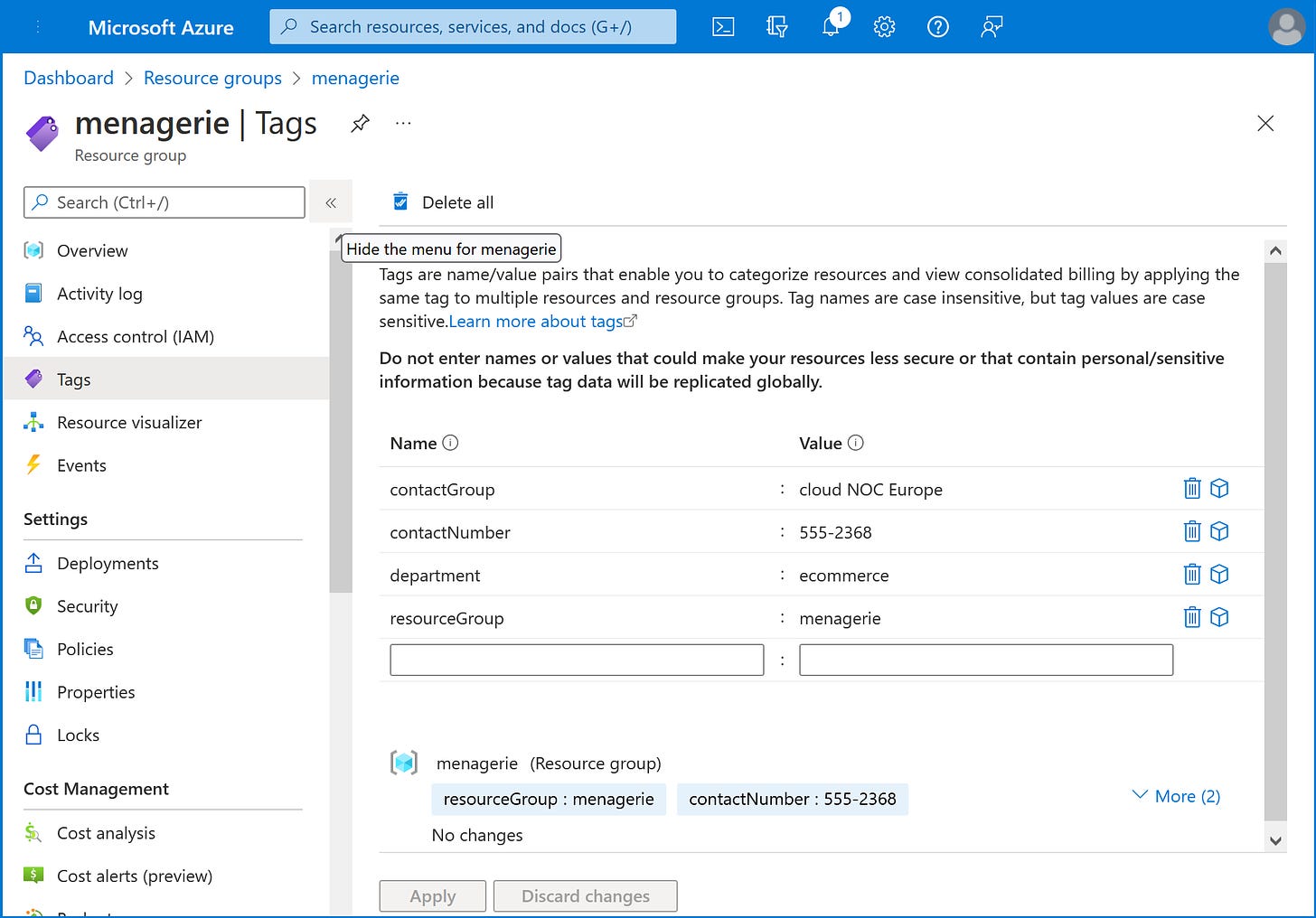
Tagging the assets
Microsoft Azure supports a rich tagging environment, and they can be applied at the subscription, resource group, and individual resource levels. For this example, we’re just going to add some owner details to a resource group. So, from the Azure Portal, search for Resource Group, pick one, and then add some tags. From scarlet’s perspective, it doesn’t actually matter what you name them, or what you put in them, scarlet will import them all and pass them on to the SIEM anyway.
Connect Microsoft Azure to scarlet
In the Azure Portal, we need to register an App and create some read-only credentials, then paste these into scarlet. A step-by-step guide is available here. Once connected, scarlet will synchronize all your VM, load balancer, container farms and functions into the SIEM.
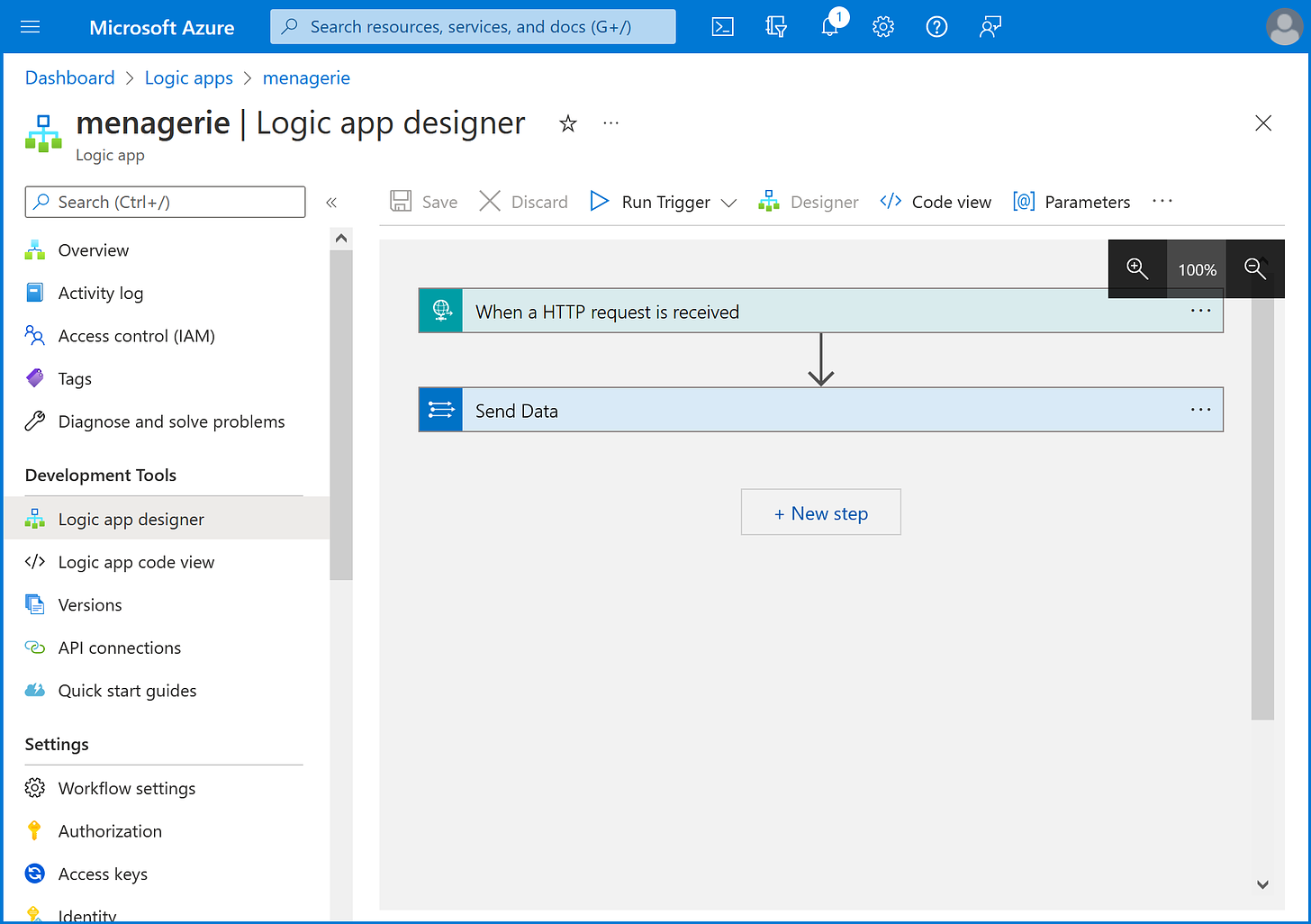
Connect Microsoft Sentinel to scarlet
In the Azure Portal, we need to create a Logic App, then paste the webhook into scarlet. Again, a step-by-step guide is available here.
Microsoft Sentinel events
And believe it or not, that is all the configuration done. From now on, whenever an event is generated within Sentinel, all the tags will be attached to the log entry, making contacting the asset owner trivial.
What next?
Our goal is to make scarlet the first choice for a high-value, low-effort way to immediately improve your security. No more forgotten servers!™
But don’t take our word for it, why not just give it a try? There’s a free, unrestricted trial available, and you only need an email address to register. You could literally be up and running, and seeing the value in ten minutes.